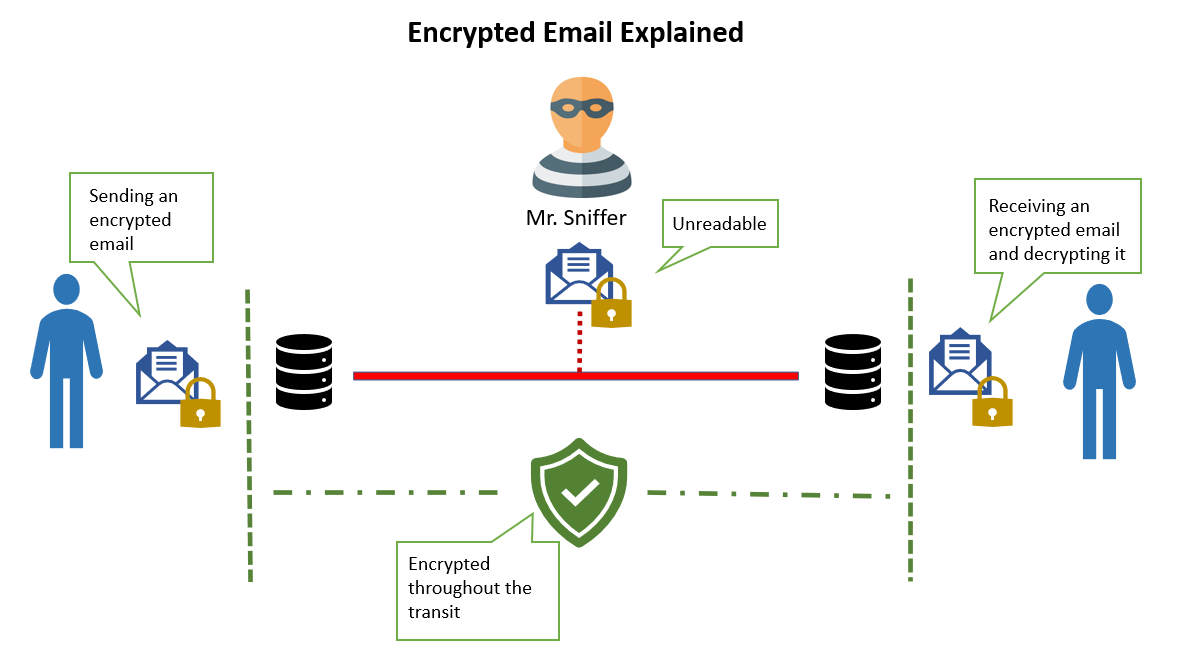
Vintage Encryption and Data Security Concept with Combination Puzzle Box or Cryptex with Secret Message Inside Stock Photo - Image of decode, compartment: 246399488

Super Security Safe Deposit Box Anti theft Lock With Encryption Keys Copper Cylinder|Wine Refrigerator Parts| - AliExpress

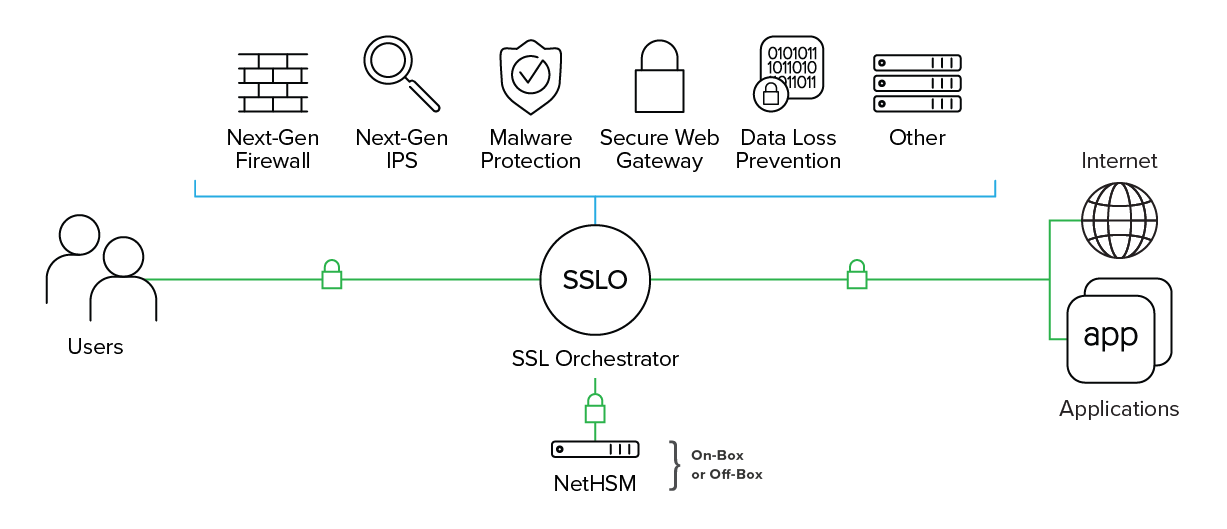
Are Encrypted Lockboxes for Data Centers Worth the Usability Cost? | Data Center Knowledge | News and analysis for the data center industry
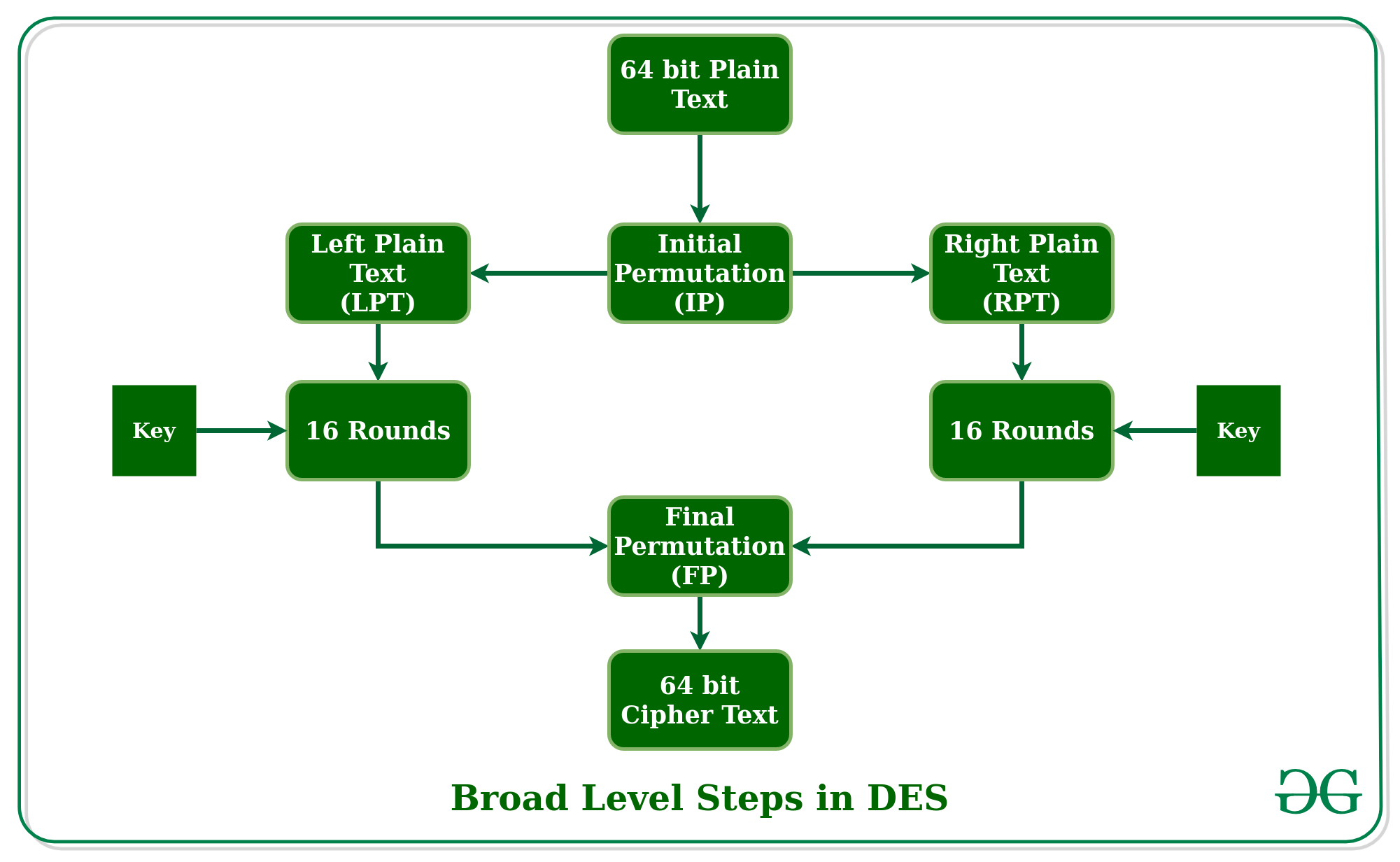
![9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book] 9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]](https://www.oreilly.com/library/view/computer-security-and/9780471947837/images/ch009-t004.jpg)
9.3 THE DES S-BOXES, P-BOX, AND INITIAL PERMUTATION (IP) - Computer Security and Cryptography [Book]

Sophos Central Device Encryption 1-Year Subscription License for Business | Technology Solutions for Small and Medium Business
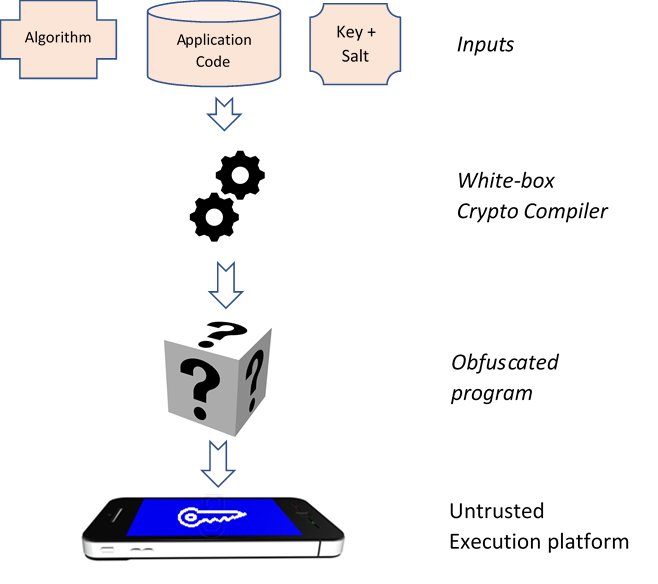
How White-box Cryptography is gradually eliminating the hardware security dependency | by Terugu Venkat | Engineering Ezetap | Medium